The AFP Phishing email is cryptolocker
In the news over the last couple of days there have been warnings of an Australian Federal Police (AFP) branded phishing email. We received one of these emails in our office and decided to run it through our malware analysis sandbox, ThreatAnalyzer, to determine the behaviour of the sample – something that wasn’t mentioned in the news articles.
Although Facebook comments have been mostly light-hearted puns from people would like to unsubscribe from from police infringement notices the malware poses a significant threat.
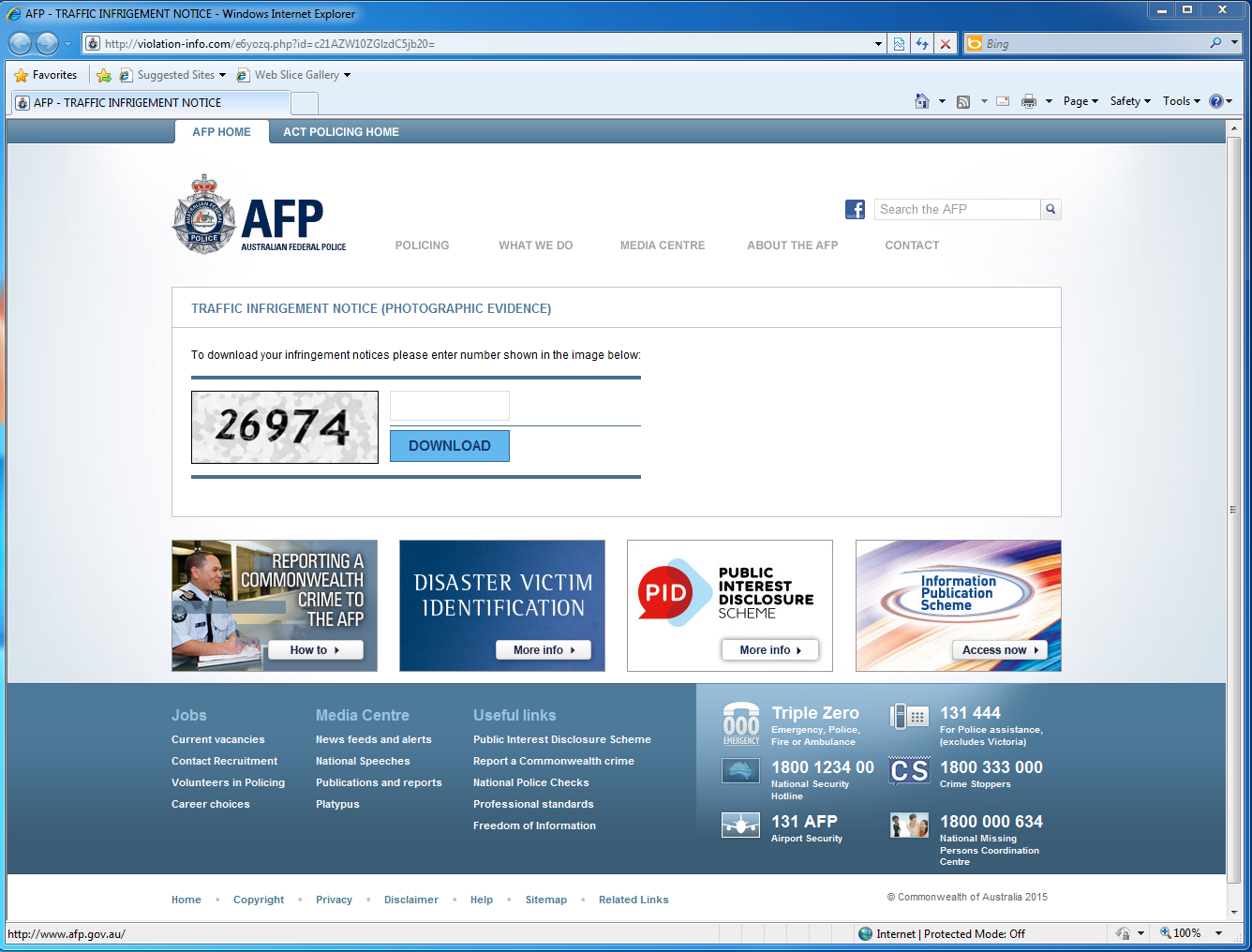
Visiting the link with-in the email provides the attacker with the targets email address as it is embedded in URL allowing the attackers to identify the individuals who have visited the the links, allowing the attackers to follow up, or in the future re-target the individuals as they may be more likely to click on these these types of links.
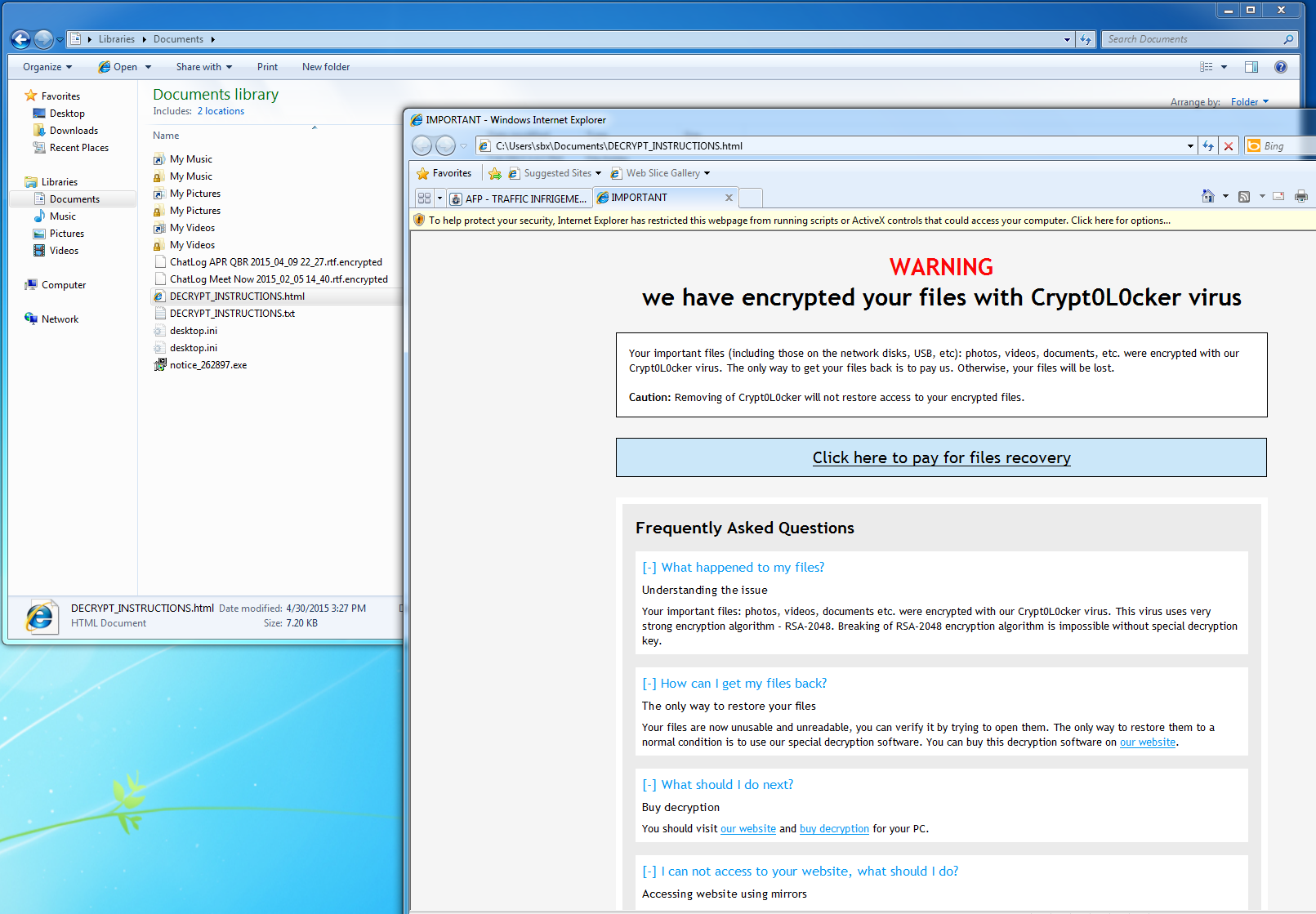
Once the page loads the victim is presented with a captcha challenge, and when it is entered they will download a zip file containing an executable file which is a variant of the well known cryptolocker virus.
When executed by the user the Cryptolocker virus will then encrypt the users files, communicate with a C&C server and the provide the user with a ransom message providing the victim with instructions on how to connect to the anonymous Tor network to make payment to be able to recover their encrypted data.
Although the various news articles urge users to update their antivirus, at the time of writing this article only 4/57 AV vendors detected the sample. None of these vendors are popular in Australia, showing that there would have been little to no protection offered to users running these solutions.
This attack is an example of how AV technology is struggling to keep up with modern malware. Preventative controls such as as Application Whitelisting would have stopped this attack by not allowing computer to execute an untrusted file. Although in this case the file was dropped as an executable, we often see the similar attacks where the spearphishing email links go directly to PDF, DOC, or Flash files which contain exploits to vulnerabilities so this is also a timely reminder to stay up to date with OS and 3rd party patching. Both these control types form part of the Australian Signals Directorate (ASD) Top 4 Mitigation Strategies.
Using a sandbox for dynamic analysis allows IT Security Administrators to quickly analyse reported phishing URLs and malware in a to determine the actions of the malware by executing the sample in a dedicated environment. Indicators such as DNS names, IP addresses and hashes can quickly be extracted and operationalised to prevent and identify future instances of the same attack, or other attacks from the same group.
For more information on sandboxing, or on how to operationalise your Threat Intelligence please don’t hesitate to contact us.