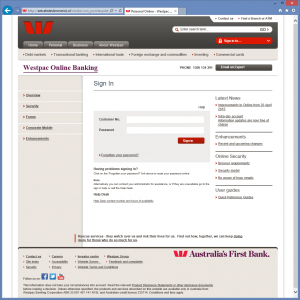
Westpac phishing email
Another suspicious phishing email was forwarded to me this morning for analysis. This one was a Westpac Phishing Email. That is, an email pretending to be from Westpac with malicious intent.
The body of the email is below:
From: WBC [mailto:[email protected]]
Sent: Wednesday, 6 May 2015 11:31 AM
To: <target email address>
Subject: 1 New payment message.This email is to confirm that you recently made a Funds Transfer to a payee with account ending 0371 for the first time.
For more information about this payment please see your transaction history.Please click here if you did not perform this transfer.
Customer <target email address>
Sincerely,
Westpac Support TeamPlease do not reply to this email. If you have questions regarding this email please contact our support area on 1300 666 656 (7am to 9pm) Monday-Friday or 9am to 6pm Saturday-Sunday AEST/AEDT).
Visiting the link takes you to a compromised Joomla site (A cafe in the Netherlands) hosting the fake website presumably used to collect Westpac customer account details to be used at a later point in time by the attacker.
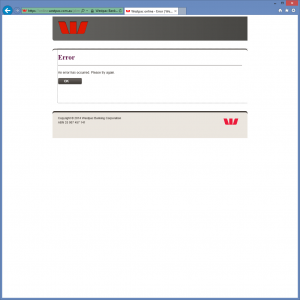
If a user enters account details they will be redirected to the to real Westpac website where they will receive an error message. Redirecting the user takes the user off the site hosting the fake website, and gives them the a secure connection showing them the “Green bar” for peace of mind.
Interestingly this redirect could allow Westpac to parse their log files, or website referral analytic to determine how many of their customers may have been at risk.
emt Distribution distributes ThreatAnalyzer, a dynamic behavioural sandboxing solution that can be used to safely analyse these emails and and also ThreatQ: An on-premise threat intelligence platform (TIP) that automates, structures, and manages all of your cyber threat intelligence in a central analytical repository.