Credential harvesting attack via Ray White Real Estate
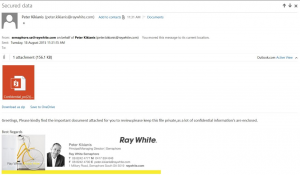
A friend forwarded me an email that she was suspicious of that she received from Ray White Real Estate. As a member of their mailing list, and not a direct correspondent of the sender, she was rightfully suspicious of the content of the email and had already contacted the Ray White branch who confirmed they were experiencing an incident, but on advice from IT were not planning to notify their customers at the current moment in time.
Ignoring the discussion for the need of mandatory breach notification in Australia, we’ll run through the stages of the attack below.
Although the language in the email (seen below) is a little rough, there is mention of an important attachment and a “confidential” document attached, and the sender and headers of the email appear to legitimate.
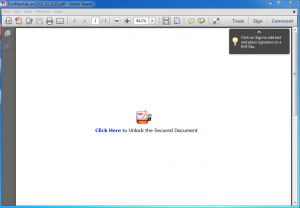
I ran the attached PDF file through our local ThreatAnalyzer dynamic analysis sandbox to run the file in a safe environment and determine if the file contained an exploit. In this case, the document itself was benign, however it masquerades as Acrobat Secure document, with a Goo.gl shortened link which redirected to a compromised website containing a credential harvesting portal. If the recipient enters credentials into the form they are stored by the server, and the user is redirected to a legitimate website hosting a journal article on sustainable investing which may be of interest to the recipient.
With credentials harvested the attacker would be then be able to access the online service that credentials were provided for at their leisure.
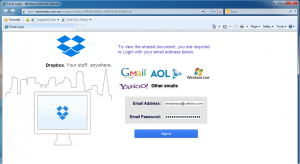
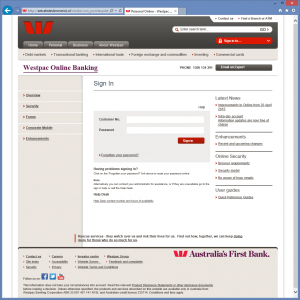
The credential harvesting landing page. What don’t you want to give us credentials for? Gmail? Dropbox? Yahoo?
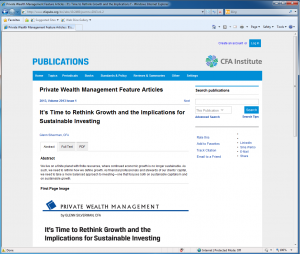
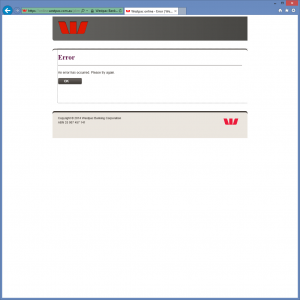
The page the user is redirected to after entering credentials, thinking they have logged on to gain access.
The fact that the attackers used a Goo.gl shorted domain allows us to run analytics on the URL using the Google API. These gave very interesting metadata of visitors who had visited the link from the PDF document. The results showed at the time of writing there had been 701 visits to the credential harvesting portal via the document and that large majority of targets (667) were from Australia. This aligns with target mailing database of an Australian Real Estate database. Also of interest was that the API revealed the timestamp of when the shorted URL was created (2015-08-18T01:11:32 – Today).
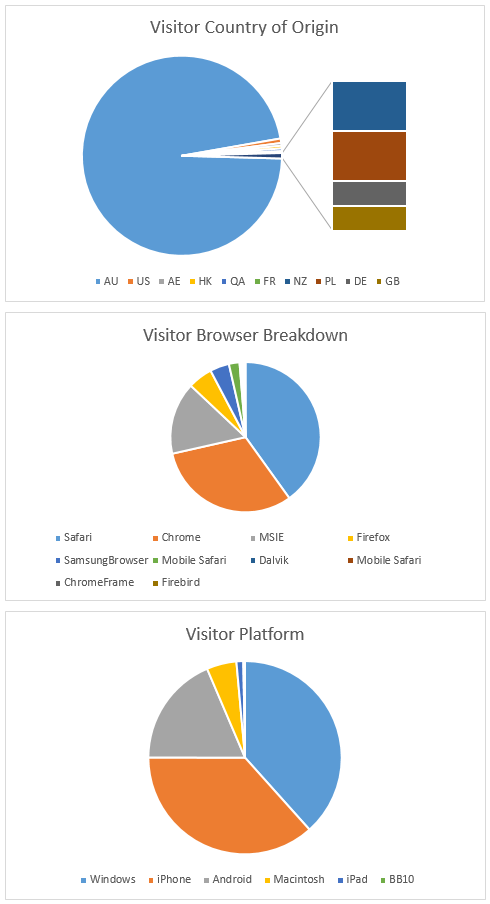
Suprisingly you can get detailed analytics from a Google shortened URL, even if you are not the creator.
In this case there was not actual malware in the attack, rather it was a multi-stage social engineering attack using a “trusted” sender as the source. Blocking Goo.gl shortcodes, often used in malware, may possibly interfere with other valid uses for them, and the domain for the harvesting portal were not known bad (at least via VirusTotal) at the time of this post being published.
We will keep an eye on our OSINT feeds over the next couple of days to see if the domain ends up being flagged as malicious/compromised and continue to monitor the analytics for the URL.