Australian Signals Directorate – “Security patching is key”. How compliant are you?
The Australian Signals Directorate (ASD) consider the timely deployment of application patches a core function in IT management. Security Patching is key to reducing an organisation’s vulnerability level on applications and operating systems.
In fact, the ASD currently rates application patching as one of the most effective security practices agencies can perform to mitigate targeted cyber intrusions.
Even so, we continually see organisations failing to implement a strategy to effectively manage this ongoing challenge.
Did you know?
The majority of successful cyber-attacks use publicly known vulnerabilities for which a patch is available. This means that a good portion of these attacks could have been avoided if companies and organisations had used vulnerability intelligence to mitigate the risks.
Want to find out how vulnerable your organisation is?
Get a Quick Scan – we can tell you in just a few minutes how secure you actually are.
If you’d like to learn a bit more first, contact us for more information.
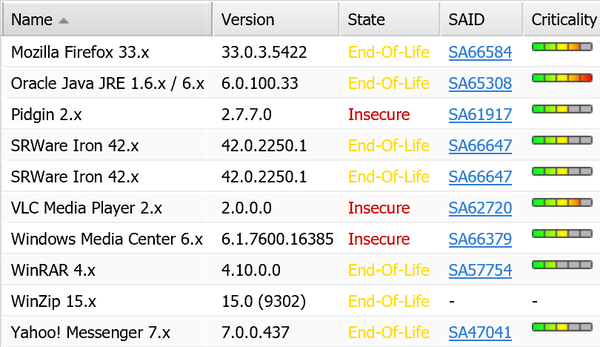
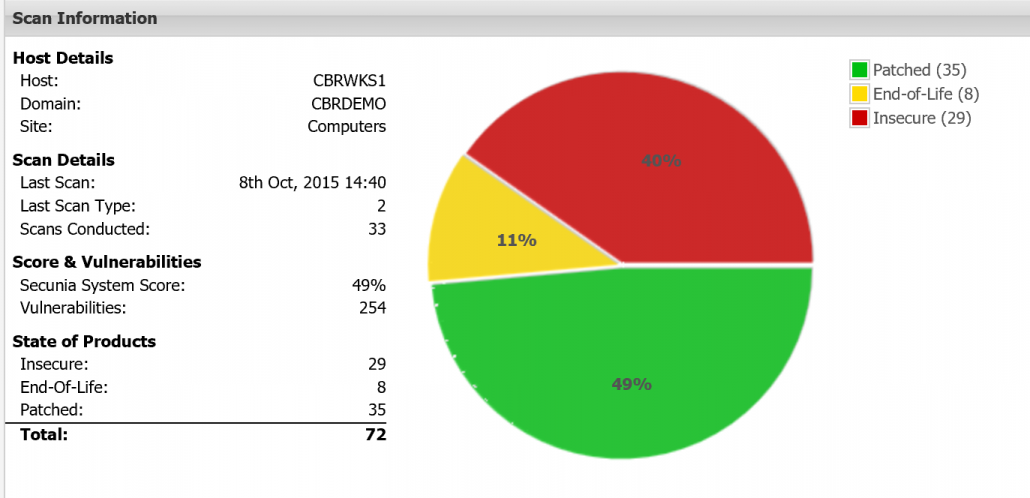
Quickscan results showing the 3rd party application risk in your environment.
How can we help?
The Corporate Software Inspector from Secunia (now part of Flexera Software) is the intelligent
solution to manage your security patching, enabling you to assess, prioritise and execute software vulnerability remediation to reduce risk. CSI tells you the when, where, what and how of security patching and alerts you you when a software vulnerability with an available patch is threatening your infrastructure, where it will have the most critical impact, what the right remediation strategy is and how to deploy it.
The Corporate Software Inspector lets your team know what to patch for maximum impact and consistent risk reduction. You get complete visibility of your systems, stay current and reduce the cost of your patch process significantly.

