Let’s patch FileZilla using System Center 2012 R2!
While patching Microsoft applications these days might be easy using System Center or WSUS, non-Microsoft applications usually get forgotten. With the vast majority of vulnerabilities being present in your non-Microsoft applications you can no longer simply take a guess at what to package up. How easy is it using a tool that has been specifically created for this problem? Let’s patch FileZilla 3.0.2.1 to 3.7.3
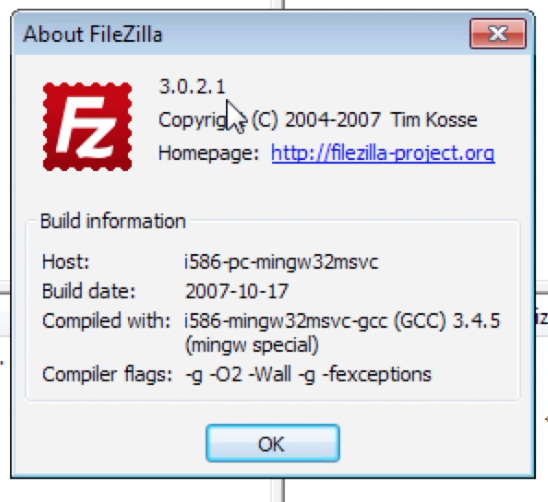
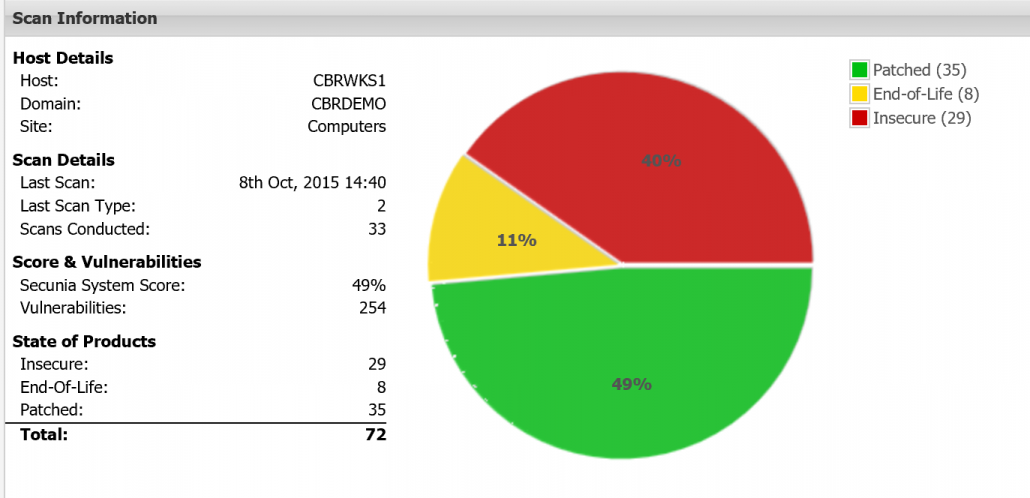
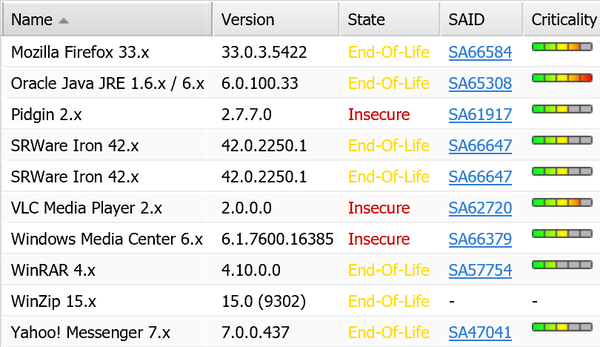
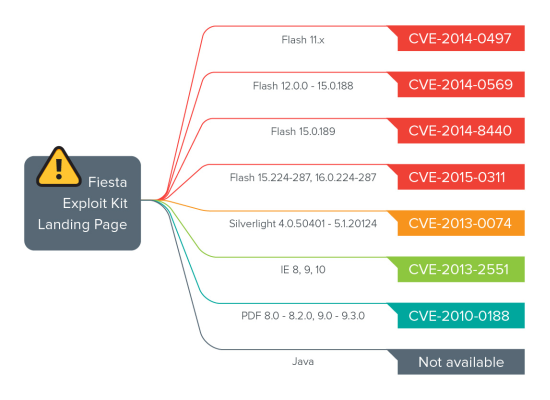
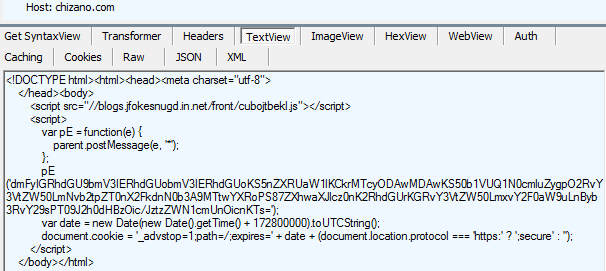
Out of date versions are a security issue
The process of patching using the Flexera Corporate Software Inspector is very easy, with it setup the data for the machine was already in the handy System Center plugin and asking to be updated:
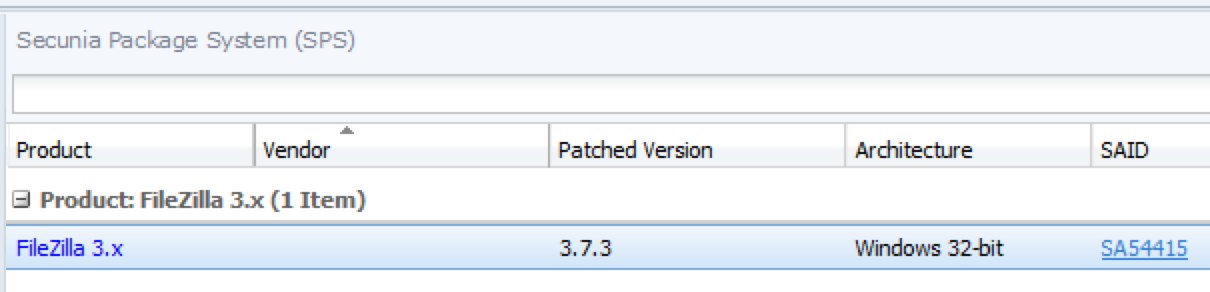
The SPS is a dynamic list, only showing you what your environment needs unlike a traditional catalogue
Using the wizard the process was as simple as “next, next, publish” and the package was created:
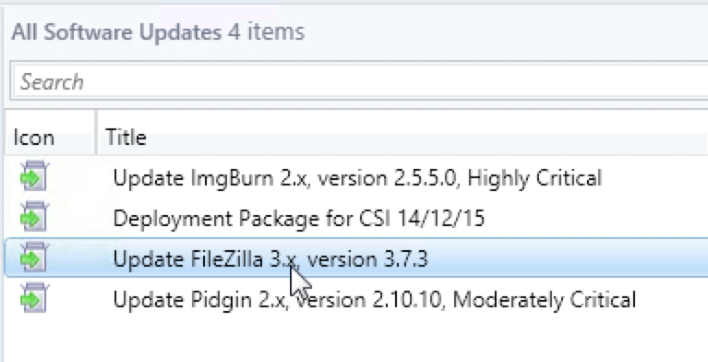
Did you know you can also drive auto deployment rules?
Finally we deploy the package via System Center:
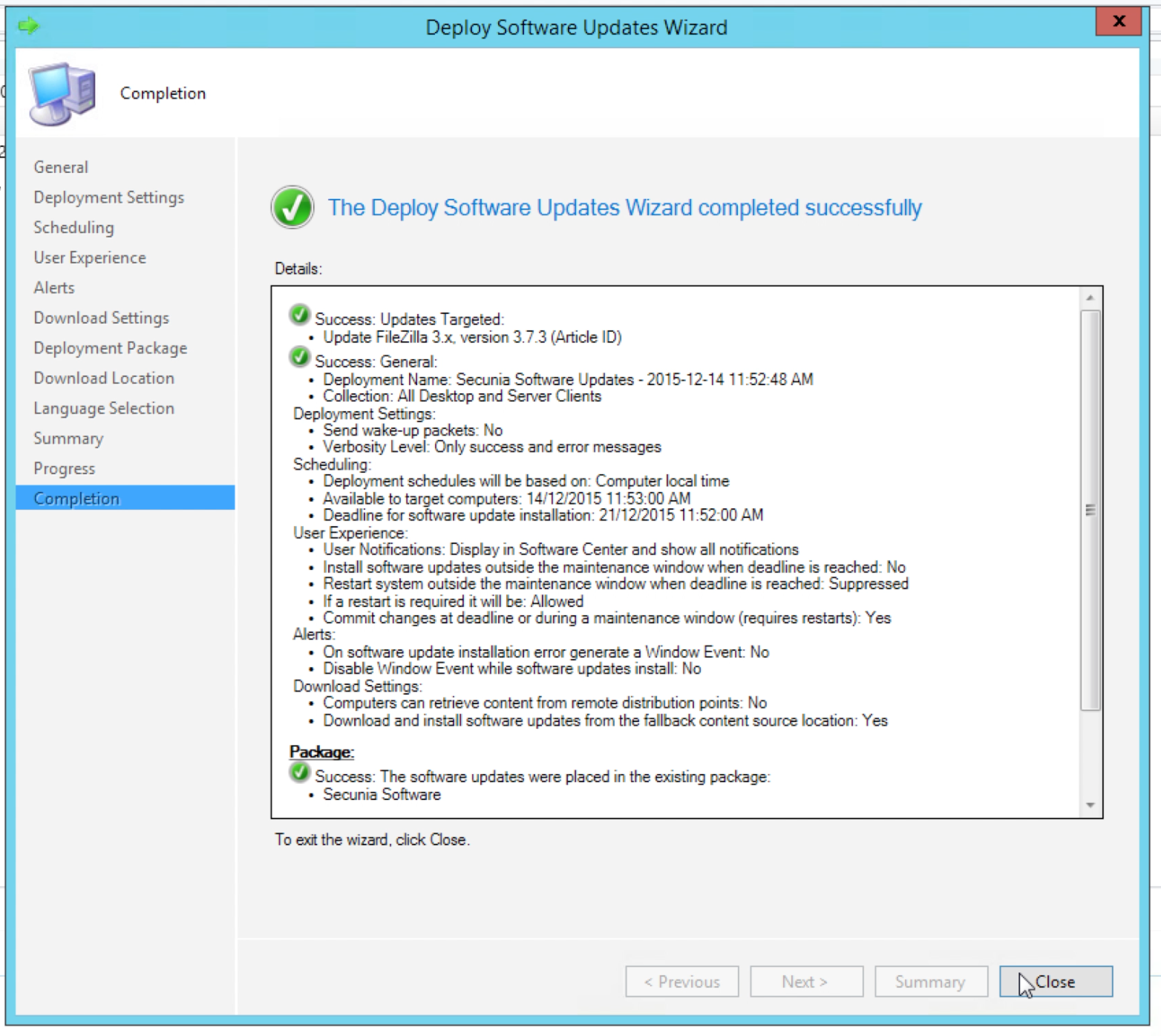
Deployment is no different to a Microsoft patch!
From here you use the built in configuration manager options to deploy the software (patch FileZilla), either by a deadline, or by when the end user wants it:
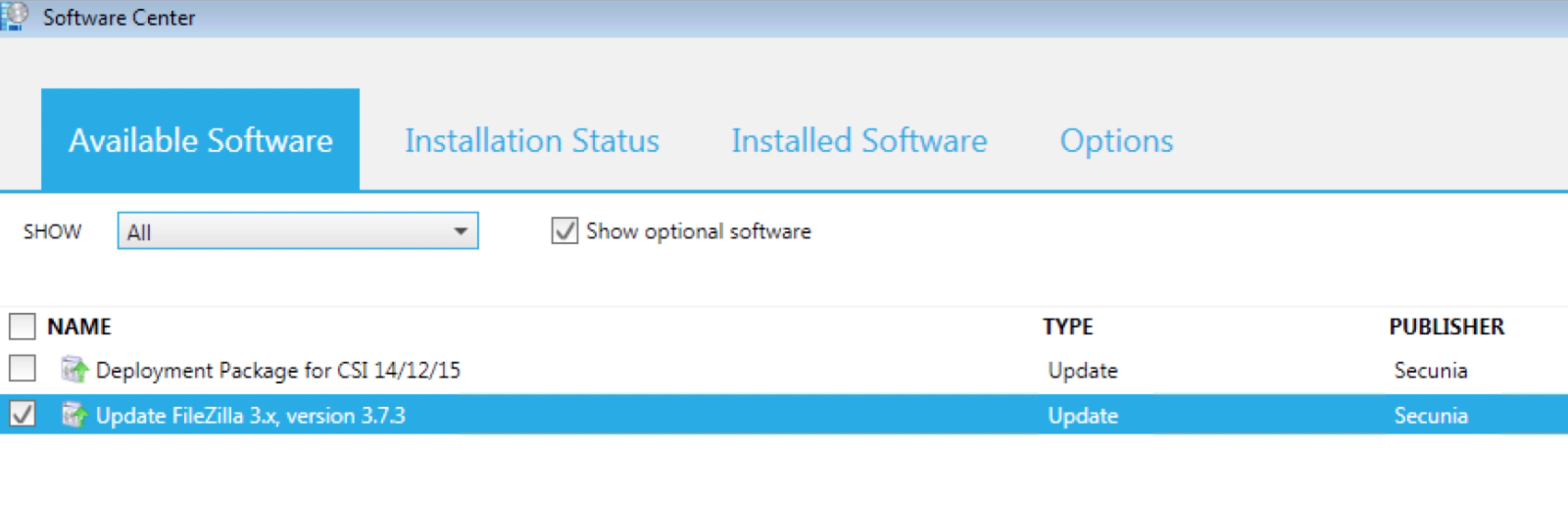
Deadlines and maintenance windows can be used like normal
And we are done!
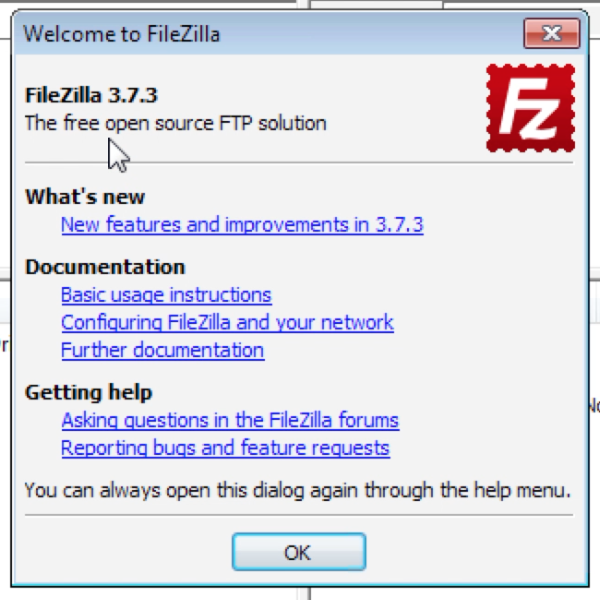
The process took only a few minutes!
If you would like to see more on how to patch FileZilla, including the wizard and also the huge database of products ready to be deployed, contact us for more information!
Update 1:
Below is the video of me conducting this, only 2 minutes long!