NEW! Acunetix 2020 Web Vulnerability Report- Insights for Web and Application Developers
Every year, Acunetix publishes an in-depth report of the most common web security vulnerabilities and network perimeter vulnerabilities. Download the Report HERE
Their annual Web Application Vulnerability Report is based on real data taken from Acunetix Online. Analysts at Acunetix uses a random selection of websites and web applications protected using their in-house software, anonymise the web apps and websites, and perform statistical analysis. Although this data is global, it still provides insights into key trends and industry analysis into issues affecting ANZ web developers and application developers.
This annual report is a must-read document for Web Developers, Application Developers, IT Administrators, Dev Ops, and even C-level Security Officers. Essentially, any organisation based in Australia and New Zealand that is implementing a robust and active cybersecurity strategy will benefit from downloading this report.
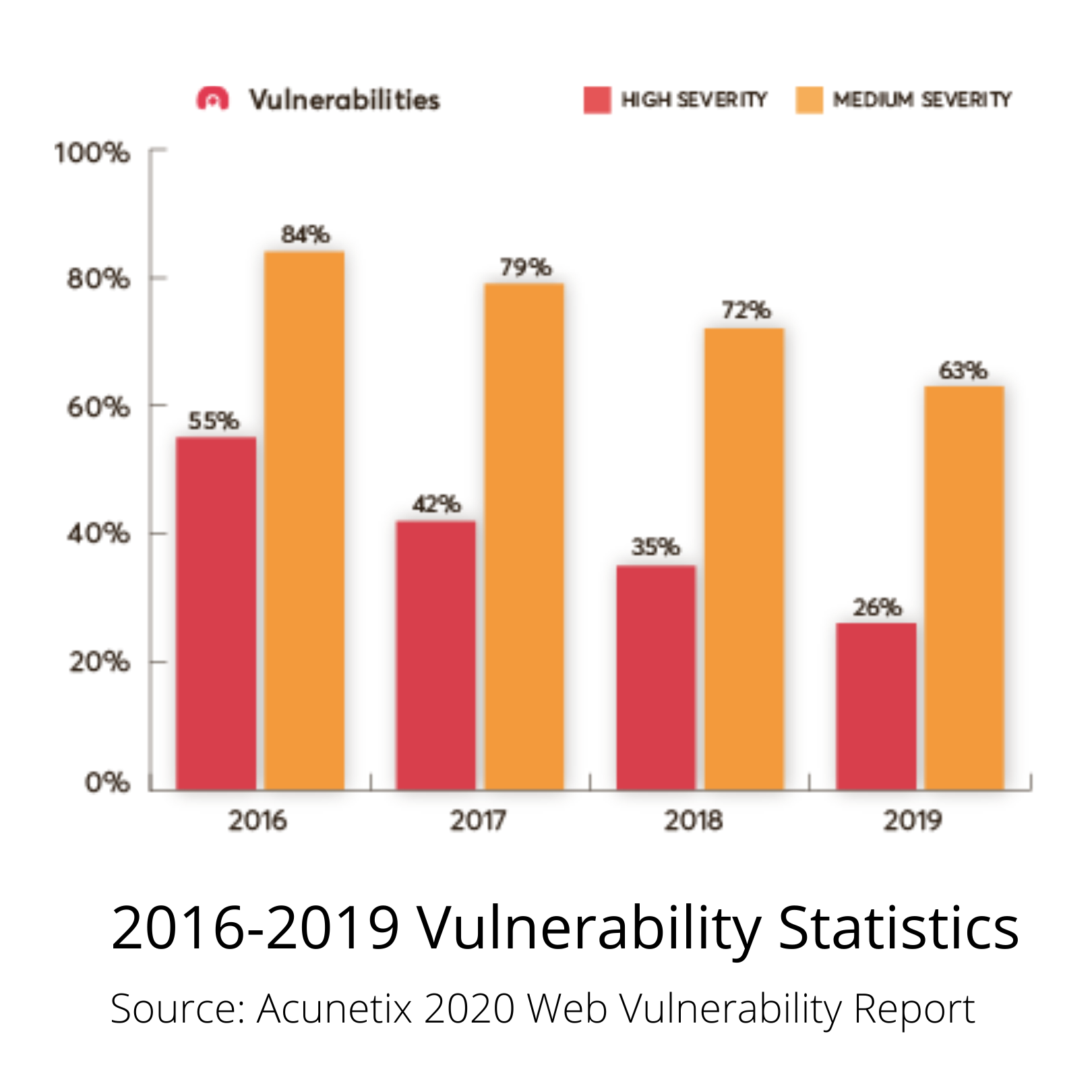
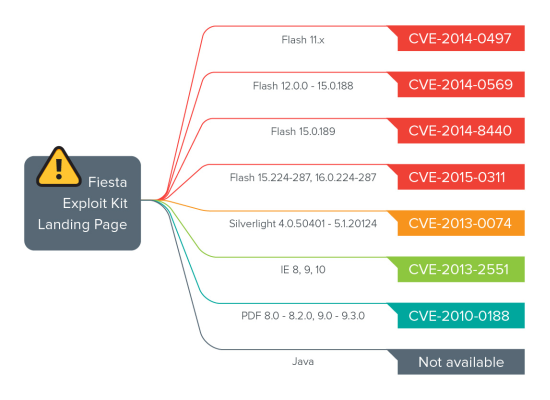
Acunetix Web Vulnerability Data
Acunetix’s findings from 2020 indicate there has been a 30% reduction in the number of vulnerabilities. However, while the numbers were lower, most newer applications and targets still demonstrated high counts of vulnerabilities. While the overall security of web applications and websites seem to be improving, there are still significant security flaws that need to be addressed. The report reveals that 25% of web applications and websites from 2020 have Cross-site Scripting (XSS) vulnerabilities, vulnerable JavaScript libraries, and WordPress-related issues. The 2020 Web Vulnerability report finds that newer developers do not have the knowledge that is required to avoid vulnerabilities, additionally, developers who are working within a development structure that does not promote web security continue to pursue development strategies that are not secure.
Acunetix 2020 Web Vulnerability Report does a deep dive into Remote Code Execution, SQL Injection (SQLi), Weak Passwords, and Missing Brute-Force Protection, Server-side Request Forgery, Perimeter Network Vulnerabilities, DoS-related Vulnerabilities, TLS/SSL Vulnerabilities, WordPress (and Other CMS) Vulnerabilities, Web Server Vulnerabilities and Misconfigurations and other specific vulnerabilities
Download the Report HERE
Interested in learning more about Acunetix v13? Watch the Video
Source: https://www.acunetix.com/acunetix-web-application-vulnerability-report/