The 3 Types of Cyber Threat Intelligence – Which one are you using?
By Alex Duffy, CSO emt Distribution
CYBERTHREAT INTELLIGENCE (CTI) is not a buzz-phrase; it’s an essential pillar of a mature cybersecurity strategy. When used and applied correctly, CTI can help security teams prepare for, and defend against, the evolving threat landscape. CTI gives organisations evidence-based, mature and effective cybersecurity strategies.
There are levels of maturity to using and understanding CTI. With each level of maturity, the context and analysis of threat intelligence becomes deeper and more sophisticated, caters to different audiences, and requires more investment.
CTI comes in three levels: tactical intelligence, operational intelligence and strategic intelligence.
Tactical intelligence is the level most commonly used by organisations and represents first level maturity of cyber threat intelligence. It is based on real-time events, investigations and/or activities and provides day-to-day support to operations. Many may use it in their security information and event management (SIEM) tools or on perimeter firewalls, and it consists of indicators of compromise, and files hashes, malicious IPs and domains. These usually have a short life span, as IPs and domains can be repurposed or taken down in days or even hours.
Operational intelligence is data that is designed to drive your day-to-day decision making, resource allocation and task prioritisation. It contains the technical direction of threat actors, indicators of targets and can contain the threats malicious tactics, techniques and procedures (TTPs). Operational intelligence has a longer shelf life because adversaries can’t change their TTPs as easily as they can change their tools like types of malware they use.
Cybersecurity professionals that manage vulnerability management, incident response and threat monitoring are the biggest consumers of operational intelligence as it can help them focus and prioritise their work.
Strategic intelligence is high-level cyber intelligence, usually containing information about foreign policy, global events and internet-based risks against organisations. This intelligence is vital for C-suite executives to allocate budget and align their cyber goals towards real-world objectives. For example, a mining company can review the analysis that the mining sector is under increasing attacks, and can then react appropriately by investing resources into strategic cyber defences.
Strategic intelligence tends to be the hardest form of intelligence to collect. It requires human collection and analysis to understand both cyber security and the worlds geopolitical situation. Strategic intelligence is usually consumed through the use of reports.
CTI increases your organisation’s ability to not only defend itself against current attacks and threats, but also to predict future attacks. The trick is to choose the right intelligence for your needs, and to make the sheer volume of intelligence actionable, whether it be reactive, proactive or futureproofing.
See how Flashpoint and ThreatConnect can help you incorporate all three levels of cyber threat intelligence
_________________________
This is an extended post from our original article which was first published in AISA.org’s Cyber Cyber Conference Magazine.
Threat Intelligence Platforms 101

By Alex Duffy, Security Solutions Architect, emt Distribution
 Threat Intelligence is quickly becoming one of the most powerful ideas in our current IT security landscape. Threat Intelligence allows you context for your data and helps empower your organisation to develop a proactive cyber security posture and strengthen overall risk management policies. It also helps security teams make more informed decisions during and in the aftermath of cyber-attacks.
Threat Intelligence is quickly becoming one of the most powerful ideas in our current IT security landscape. Threat Intelligence allows you context for your data and helps empower your organisation to develop a proactive cyber security posture and strengthen overall risk management policies. It also helps security teams make more informed decisions during and in the aftermath of cyber-attacks.
So, you may already have a plethora of security products in place like Firewalls, Proxys and endpoint security, but are you able to see the big picture? With all of these security products logging back to your Security Information and Event Management (SIEM) it can come across as just noise. How can you evaluate if that IP address or domain is important to you?
Your trusty SIEM is collecting data, but do you know what it’s collecting or how important it is? Maybe, you may have the SIEM using a lookup list so when it detects a bad IP it will alert you. Great, that’s a good start, but WHY is it a bad IP? Is it part of a larger attack? Is it just the beginning stages in the cyber kill chain? This is where context becomes key, linking into why Threat Intelligence is critical.
Rudimentary threat Intelligence can be achieved manually. An example being identifying an IP address you want to find out more information from, and then using the internet and your security sources to build a picture around it. But what if you want more comprehensive analytics, then you will need automation, which brings me onto my next point;
What is a Threat Intelligence Platform (TIP) and why do you need one?
 The human element is the slow part in threat intelligence. The human brain, although magnificent can often not compete with the ease and functionality of an automated system. Besides, why waste your Security Analyst’s precious hours when you can have half the cumbersome work done for you. Threat Intelligence Platforms (TIP) allow you to pass off key information like IPs and URLs that are important to you and build context on them using a large number of open source threat feeds and open source blocklists. A TIP becomes your single pane of glass to the security of your organisation. For example, you have seen a URL come through the proxy, and you have identified through the TIP that it is related to a malware campaign that re-uses their infrastructure and domain names for the command and control (C2) portion of their attack. By using this information, you now know that a device in your network is infected and you can begin the process to clean it up. TIPs make
The human element is the slow part in threat intelligence. The human brain, although magnificent can often not compete with the ease and functionality of an automated system. Besides, why waste your Security Analyst’s precious hours when you can have half the cumbersome work done for you. Threat Intelligence Platforms (TIP) allow you to pass off key information like IPs and URLs that are important to you and build context on them using a large number of open source threat feeds and open source blocklists. A TIP becomes your single pane of glass to the security of your organisation. For example, you have seen a URL come through the proxy, and you have identified through the TIP that it is related to a malware campaign that re-uses their infrastructure and domain names for the command and control (C2) portion of their attack. By using this information, you now know that a device in your network is infected and you can begin the process to clean it up. TIPs make
Great, you now have a TIP, so what are your next steps? Automation. This will allow you to leverage the TIP to help make better informed decisions and then take action. In the above example I said that we saw a C2 URL in the proxy, and by using the TIP we have determined that it is malicious. Following this, and using automation, we can block said URL, either with or without human interaction.
But most importantly a TIP can parse through massive amounts of your data, provide context for your security logs, and focus your efforts in stopping real world threats. Last but not the least, A TIP optimises response time and improves remediation, and reports strategic, operational and tactical intelligence to stakeholders.
This all sounds cool right? Learn more about Threat Intelligence at our live webinar on April 17th. This interactive webinar is perfect for a security professional who wants to quickly identify real threats to their organisation, even if they don’t have the budget to build out a dedicated threat intelligence team.Register Here
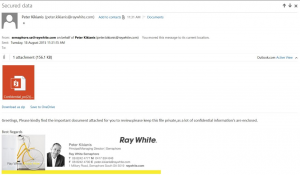
Credential harvesting attack via Ray White Real Estate
A friend forwarded me an email that she was suspicious of that she received from Ray White Real Estate. As a member of their mailing list, and not a direct correspondent of the sender, she was rightfully suspicious of the content of the email and had already contacted the Ray White branch who confirmed they were experiencing an incident, but on advice from IT were not planning to notify their customers at the current moment in time.
Ignoring the discussion for the need of mandatory breach notification in Australia, we’ll run through the stages of the attack below.
Although the language in the email (seen below) is a little rough, there is mention of an important attachment and a “confidential” document attached, and the sender and headers of the email appear to legitimate.
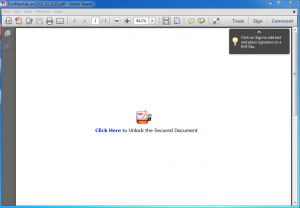
I ran the attached PDF file through our local ThreatAnalyzer dynamic analysis sandbox to run the file in a safe environment and determine if the file contained an exploit. In this case, the document itself was benign, however it masquerades as Acrobat Secure document, with a Goo.gl shortened link which redirected to a compromised website containing a credential harvesting portal. If the recipient enters credentials into the form they are stored by the server, and the user is redirected to a legitimate website hosting a journal article on sustainable investing which may be of interest to the recipient.
With credentials harvested the attacker would be then be able to access the online service that credentials were provided for at their leisure.
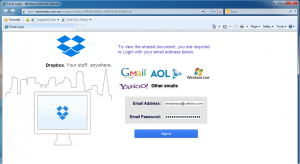
The credential harvesting landing page. What don’t you want to give us credentials for? Gmail? Dropbox? Yahoo?
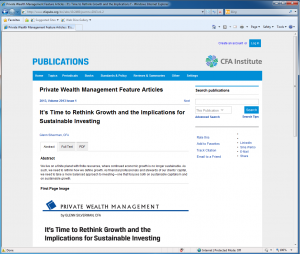
The page the user is redirected to after entering credentials, thinking they have logged on to gain access.
The fact that the attackers used a Goo.gl shorted domain allows us to run analytics on the URL using the Google API. These gave very interesting metadata of visitors who had visited the link from the PDF document. The results showed at the time of writing there had been 701 visits to the credential harvesting portal via the document and that large majority of targets (667) were from Australia. This aligns with target mailing database of an Australian Real Estate database. Also of interest was that the API revealed the timestamp of when the shorted URL was created (2015-08-18T01:11:32 – Today).
Suprisingly you can get detailed analytics from a Google shortened URL, even if you are not the creator.
In this case there was not actual malware in the attack, rather it was a multi-stage social engineering attack using a “trusted” sender as the source. Blocking Goo.gl shortcodes, often used in malware, may possibly interfere with other valid uses for them, and the domain for the harvesting portal were not known bad (at least via VirusTotal) at the time of this post being published.
We will keep an eye on our OSINT feeds over the next couple of days to see if the domain ends up being flagged as malicious/compromised and continue to monitor the analytics for the URL.
RSA 2015: SIEM and logging solutions are dead?
Last week at the RSA Conference 2015, RSA CISO Eddie Schwartz declared that in addition to Anti-Virus, SIEM solutions are also ‘dead’ and that IT security departments need to become “more big data aware“. ‘Big Data’ in this case refers to the collection and processing of data holistically in an organisations environment, not just collecting data from individual security appliances.
This comment may seem surprising on face value, however is quite telling of the current state of operational security within organisations today. When performing their work, security analysts typically respond to security alerts from a number of individual security appliances or applications on the network. This requires a lot of effort on part of the security analyst, to view each event and ask the question, what does this event mean in the context of my environment? This approach creates issues for scalability as organisations typically record thousands if not millions of events per day.
In recent years, the security industry has invested heavily in threat intelligence to try and solve this issue. Threat Intelligence helps to provide context for events and therefore reduces the amount of events analysts need to manually process.
In order to provide this context, appliances must integrate with numerous internal and external sources of information, something that traditional SEIM appliances are not built to do.
And what of the future of SIEM? According to Mr. Schwartz, “SIEM will continue to be important for organisations at some level of log management, such as the small-to-medium enterprise who are looking at it for compliance. But to deal with advanced threats and focus on the network and go by reputation, you have to go beyond the SIEM. You can build your own system with a data warehouse or you can use a managed partner, but who builds their own technology. SIEM has limited visibility.”
EMT Distribution has recently partnered with ThreatQuotient in order to provide a leading threat intelligence product to our clients. ThreatQuotient helps organisations easily enable a multitude of intelligence sources with the flip of a switch. ThreatQ is an on-premise threat intelligence platform (TIP) that automates, structures, and manages all of your intelligence in a central analytical repository.